General Information

Over 15% of new users switched from Websense. Over 20% used to run Surf Control. Ask about our competitive pricing program and find out why it literally pays to switch to Pearl Software.
QUICK TOUR
View short videos about Pearl Echo's cybersecurity features and ease of installation.PRICING
Contact the Pearl Software sales team to learn about Pearl Echo.Suite pricing options.COMPARE PRODUCTS
See how Pearl product specifications meet your requirements.
Website.Echo manages web site traffic of any Web browser on or off your network. Website.Echo is not affected by browser application changes since it does its work at the protocol level. As a standalone module or as part of Pearl Echo.Suite, Website.Echo provides advanced cybersecurity capabilities allowing you to enhance productivity and protect and conserve resources.
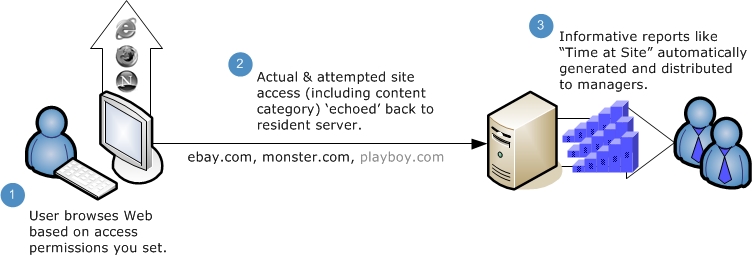
Website.Echo is packed with features for the large enterprise but remains targeted to the core needs of your growing business. The Website.Echo Report Manager provides in-depth analytics that can be customized for your existing users and groups. Features like automated report distribution, automated installation and self-administering workstation agents allow Website.Echo to meet the needs of any size organization.
Website.Echo provides a host of cybersecurity controls that can be finely tuned to your specific needs. Crypto.View, custom controls, allow and block lists, linguistics and URL filters are all available to be deployed as part of your security management strategy.
Website.Echo is a feature-rich package. Some of the latest features include:
- Echo Crypto.View™ - Monitor encrypted communications. Secure sites act just like regular web sites. They can still be filtered the same way and by the same rules. The same is true for secure email. Safely view and control encrypted data (https, ssl, etc.) without the use of complicated proxy servers or Internet traffic redirection.
- Echo Smart.Capture™ - Focus on user trends while reducing monitoring and storage of non-pertinent user web activity by as much as 96%.
- HTTPSafety.Check™ - Ensure the strength of encrypted communications.
- Safe Search - Enforce Google, Bing and Yahoo Safe Search settings.
- Workstation Installation Automation - Remotely deploy Pearl Echo agents from your Pearl Echo Administration Console.
- Web Crawler - Easily create Allow Lists with a built in search tool to identify hidden resources needed to load pages.
- Profile Investigator - Quickly report on users' profiles and active cybersecurity rules.
- Web Page Redirect - Customize what a browser displays when a user is blocked due to a security restriction.
- Advanced Report Filters - Create unlimited filters for additional report customization and more granular analytics.
- Report Classification Headings - Add customized DoD-compliant document markings with appropriate security descriptors.
- Zero 3rd-party conflicts - Run with confidence. Pearl Echo's patented cybersecurity technology integrates with Microsoft's new firewall security model.
For an exhaustive list of features, select "Show More Details" at the bottom of the Product Comparison Page.
Website.Echo Filtering Software Requirements
Workstations
- Agent Workstation Hardware Requirements
- Processor and Memory as specified by minimum Operating System requirements.
- At least 100 MB of available disk space.
- Agent Workstation Operating System Compatibility (32 or 64 bit, Host or Virtualized)
- Windows 10, Windows 8, Windows 7
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012, 2012 R2
- Windows Server 2008 R2
- Citrix Server, Microsoft Terminal Server (RDS)
Server Hardware Recommendations (Administration Machine)
- A Windows server or workstation with a fixed IP address or Fully Qualified Domain Name (FQDN).
- Example hardware specifications for a mid-size implementation (250 users) include:
- Processor and Memory as specified by minimum Operating System requirements.
- 1 GB RAM
- At least 10 GB of free disk space
- Operating Systems Compatibility (32 or 64 bit, Host or Virtualized)
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012, 2012 R2
- Windows Server 2008, 2008 R2
- Windows 10
- Windows 8
- Windows 7
Website.Echo Software Benefits
It has been shown by Forrester Research that malware is present on 10 percent of all websites. Keep the computers on your network safe with Website.Echo's advanced monitoring and filtering functions, and benefit from the ability to totally control access to sites according to your acceptable use rules.
Website.Echo Benefits
Internet access parameters give you total control of how people on your network are using the web
If you have certain computers or groups or single users who require unique access parameters, you can easily customize for them
For adult, shopping, gaming, peer-to-peer download and other site categories, you can easily designate and set access permissions
Thorough reports are generated to keep auditors, users and management apprised of Internet usage activity
You can specify time controls for web access that prevent computers that are unattended after hours from being used
Websites and domains that you trust and know are safe can be exempted from your "blocked" list. You can also block certain domains that exist in categories that are openly available
By using Echo.Filters, you're able to maintain your list of blocked domains automatically
Categorize and monitor the browsing habits of your users and instantly know how much time they spend surfing the Internet
More Info
Details
Architecture
Configuration
Crypto.View™
Echo.Filters™
Reports
Mobility Monitor™
HTTPSafety.Check™
Citrix & Terminal Server
SQL Server
Product Data Sheet
Product Pricing and Comparison
Support & Updates
Pearl Echo FAQ
Knowledge Base
Product Patches
User's Guide
Sample AUP
Starter Block Lists
