Local Area Network or VPN Configuration
The computer on which you install the Website.Echo Server Software must have an IP address that is visible to managed workstations. When you run Website.Echo for the first time, the Setup Wizard will ask you the IP address of your server and a service port number.
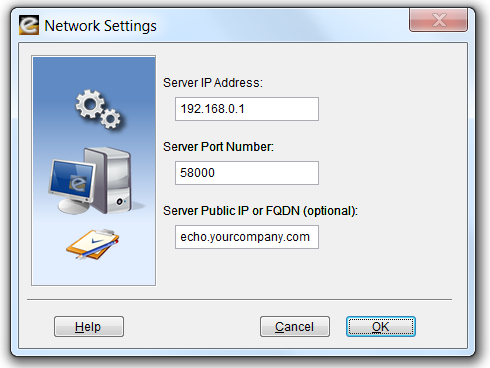
This IP address and port number will also be used during your automated workstation installations. If you would like to monitor users that roam beyond the perimeter of your private network, enter the Public IP or Fully Qualified Domain Name of your Website.Echo Server.
Wide Area Network Configuration
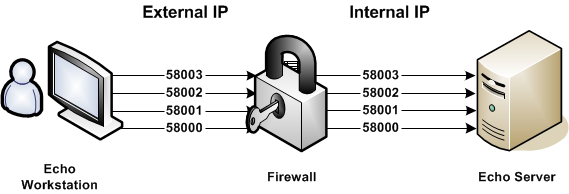
Pearl Software’s Mobility Monitor™ works with a Firewall or NAT device through a specified group of ports. Website.Echo workstations establish an initial connection with the Website.Echo Server on a Control Port (Server Port Number). Additional command and control communications occur on three supplemental IP ports. The Server Port Number (e.g. 58000) and three additional IP ports (e.g. 58001, 58002 and 58003) will need to be opened for direct pass-thru on your Firewall device.
Example
Public IP: Server Port Number + 0 «-» Private IP: Server Port Number + 0
Public IP: Server Port Number + 1 «-» Private IP: Server Port Number + 1
Public IP: Server Port Number + 2 «-» Private IP: Server Port Number + 2
Public IP: Server Port Number + 3 «-» Private IP: Server Port Number + 3
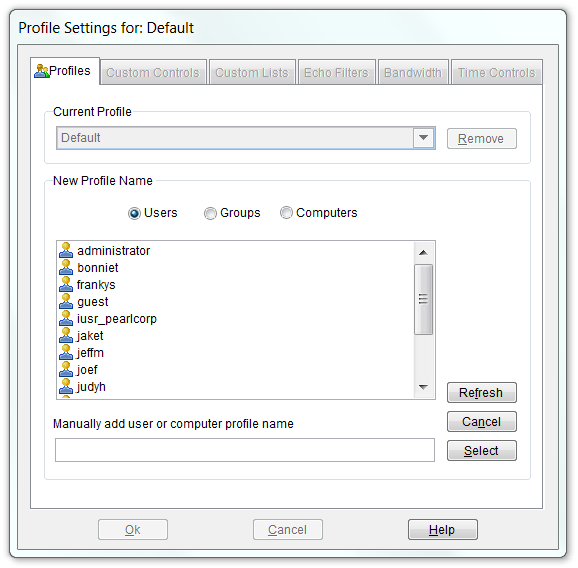
Website.Echo Control Profiles
A control profile is defined by your server's available User, Group and Computer names. When Website.Echo Server Software is installed on a machine that is part of a Domain using the Active Directory Service, Website.Echo will access and display the available User, Group and Computer names from the Active Directory database. If Active Directory Service is not available, Website.Echo will access and display the available User and Group names from the server on which it is installed. If you have not installed the Website.Echo Server software on a Windows server, you can manually create the User and Computer names of profiles that you would like to manage.
When a managed User attempts to access the Internet, their activity is governed by a Profile’s configuration settings. Website.Echo first looks for a matching User profile. If no matching User profile is found, Website.Echo looks for a Group profile to which the User belongs. If no matching Group profiles are found, Website.Echo looks for a Computer profile based on the computer name being used. If no matching Computer profiles are found, Website.Echo uses the settings defined by your Default profile. If a User belongs to multiple Groups, Website.Echo selects the first matching Group (alphabetically) to govern Internet access.
Website.Echo Control Settings
Security levels are established by selecting the appropriate button under the Web category in conjunction with entries in the Profile's Web Allow and Block Control Lists. Additional security configurations are available in Pearl Echo.Suite.
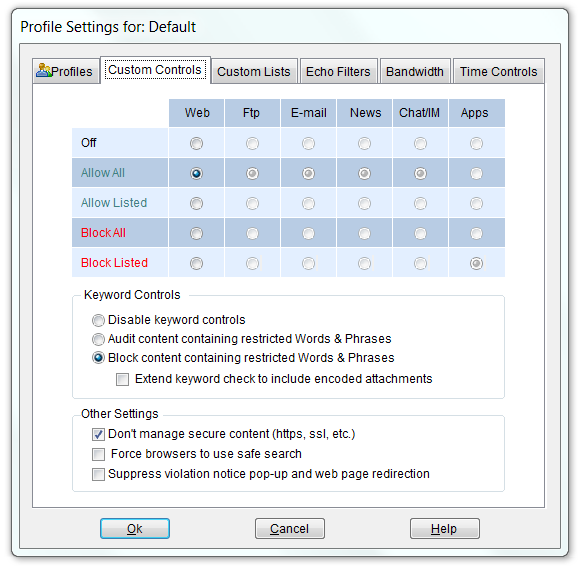
You can have Website.Echo block or audit objectionable words, phrases and text patterns by selecting "Block/Audit content containing restricted Words & Phrases." With the Block option set, Website.Echo will allow all web site content except for content containing words or phrases defined in the Profile's Words & Phrases Control list.
You can also stop users within a Profile from accessing secure Web sites by selecting “Block secure site access (https).” Pearl Echo logs https traffic by IP address and will even resolve the IP address to a domain name when available.
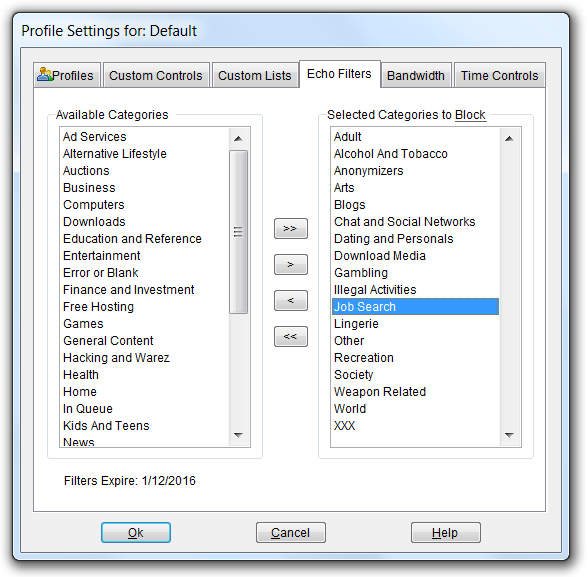
Echo.Filters™
You can block access to Web sites based on categories of content in the Echo Filters tab of the Profile window. Echo.Filters is Pearl Software’s comprehensive web URL filtering database, designed to simplify the administration of Internet use. Using the Echo.Filters module, administrators can choose from over forty categories that they wish to block as well as run reports on users accessing web sites in these categories.
The optional Echo.Filters URL module allows administrators to set specific access rules to Web pages based on the pages’ categorized content. Automatic updates to the URL database are done constantly as our proprietary search algorithms scour over 1.6 terabytes of Web content each month looking for inappropriate or harmful content including malicious sites that are typically the genesis of most malware applications that infect end-user devices. Don't fight malware after its already made it to the desktop. When Pearl Software scans a site we also download and check for viruses in setup files, zip files and executable files. If viruses are found, the site is added to one of Echo.Filters malware-related categories to prevent a seemingly harmless site from launching a drive-by install of malicious code or providing a fake hardware driver.
99.9% of the Active Web - For every million websites our customers visit, over 99.9% of them are already categorized in the Echo.Filters URL database. When an end user requests a new Internet web site or a website that is not already in the Echo.Filters URL database, it is added to the review queue for review. Our proprietary ranking algorithm adds the more commonly requested websites to the top of the queue with the most popular being reviewed and added to the master database within 24 hours.
Download a Free Trial ...to get a hands-on look at Pearl Echo's features and functions
Start the Pearl Echo.Suite Product Video Tour ...to get a quick look at Pearl Echo's capabilities without installing.
View Pearl Software vs. Competition ...to see how Pearl Software stacks up to the competition.
Request a Quote ...to receive personalized pricing that matches your requirements.
