General Information

IM.Echo monitors Skype IM at the network layer. Attempts to use screen shots or keystroke loggers are incomplete and unworkable for comprehensive cybersecurity and in-depth analytics. Try a 14-day, no risk evaluation.
QUICK TOUR
View short videos about Pearl Echo's cybersecurity features and ease of installation.PRICING
View IM.Echo licensing and options.COMPARE PRODUCTS
See how Pearl product specifications meet your requirements.
Organizations need to protect sensitive information and prevent its inadvertent disclosure. Examples include financial data or personally identifiable information (PII) such as credit card numbers, social security numbers, or health records. With IM.Echo’s data loss prevention (DLP) for Skype, you can identify, monitor, and automatically protect sensitive information.
Used by itself or in conjunction with Pearl Echo.Suite, IM.Echo lets you easily customize your cybersecurity policies for comprehensive Skype IM traffic control.
Want to see what's being written in Skype IM or Group Chats? IM.Echo's Quick Link function allows you to do this by restoring both outgoing and incoming text. It creates a complete activity history for you to review.
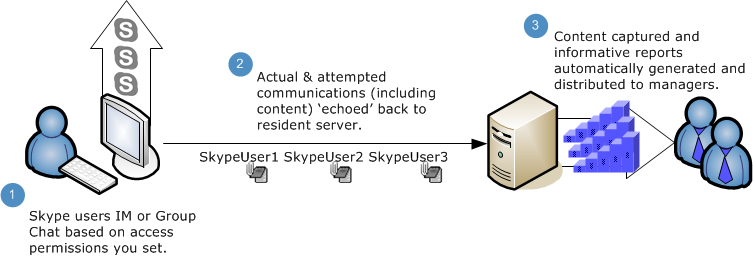
We were thinking "enterprise" when we created IM.Echo. Included is a report manager that generates customizable analytics for groups and users. To prevent leaks that are confidential or personal, the product includes a text pattern analyzer. The need to control Skype instant messaging activity is clear: while it's a handy tool for communications across the network, it can be a cybersecurity hole for insider threats as well as cause the loss of productivity when not used in in accordance with policy.
IM.Echo Chat Control Software Requirements
Workstations
- Agent Workstation Hardware Requirements
- Processor and Memory as specified by minimum Operating System requirements.
- At least 100 MB of available disk space.
- Agent Workstation Operating System Compatibility (32 or 64 bit, Host or Virtualized)
- Windows 10, Windows 8, Windows 7
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012, 2012 R2
- Windows Server 2008 R2
- Citrix Server, Microsoft Terminal Server (RDS)
Server Hardware Recommendations (Administration Machine)
- A Windows server or workstation with a fixed IP address or Fully Qualified Domain Name (FQDN).
- Example hardware specifications for a mid-size implementation (250 users) include:
- Processor and Memory as specified by minimum Operating System requirements.
- 1 GB RAM
- At least 10 GB of free disk space
- Operating Systems Compatibility (32 or 64 bit, Host or Virtualized)
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012, 2012 R2
- Windows Server 2008, 2008 R2
- Windows 10
- Windows 8
- Windows 7
IM.Echo Skype Chat Monitoring Benefits
IM.Echo controls and archives all Skype for Business IM and Group Chat content and provides reporting so that administrators can maintain a log of IM activity including attempts to circumvent DLP policy.
IM.Echo Benefits
Identify sensitive information across all of your locations
Monitor and protect sensitive information in Skype for Business (Lync and Office 365)
Prevent the accidental sharing of sensitive information through Skype
Securely archive and audit all user and group Skype chat activity
Capture Skype IM text for real time content review
Tailor Skype IM access for specific AD users, groups or computers
Block or audit content based on Skype address, keyword or text pattern to stop inappropriate IM content from the user’s desktop or terminal session
View Skype DLP reports showing content that matches your organization’s DLP policies
Increase management's awareness by providing informative reports that are automatically generated and distributed to management, users and auditors
