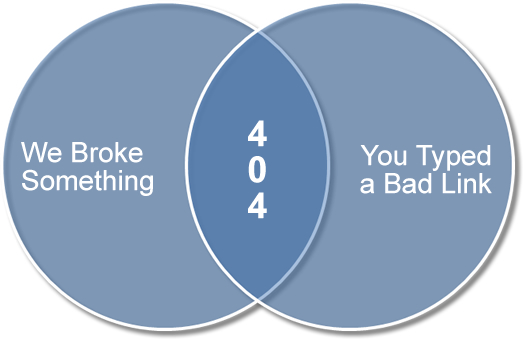
The content you requested no longer exists. You may be interested in the following updated links:

The content you requested no longer exists. You may be interested in the following updated links:
PEARL SOFTWARE || © Copyright 1996-2019 || All Rights Reserved Terms of Use and Policies
PEARL SOFTWARE || © Copyright 1996-2019 || All Rights Reserved Terms of Use and Policies