Monitor and Control Encrypted Web Sites
Ensure your cybersecurity policies remain in tact - even through encrypted communications. With Echo Crypto.View, access to secure sites is monitored and controlled just like unprotected communications. Secure web sites (HTTPS) can still be filtered the same way and by the same rules.
Website.Echo's integration into the endpoint allows Crypto.View to manage encrypted data at the endpoint. Crypto.View reconciles what the end user sees and what is sent (or attempting to be sent) over the network.
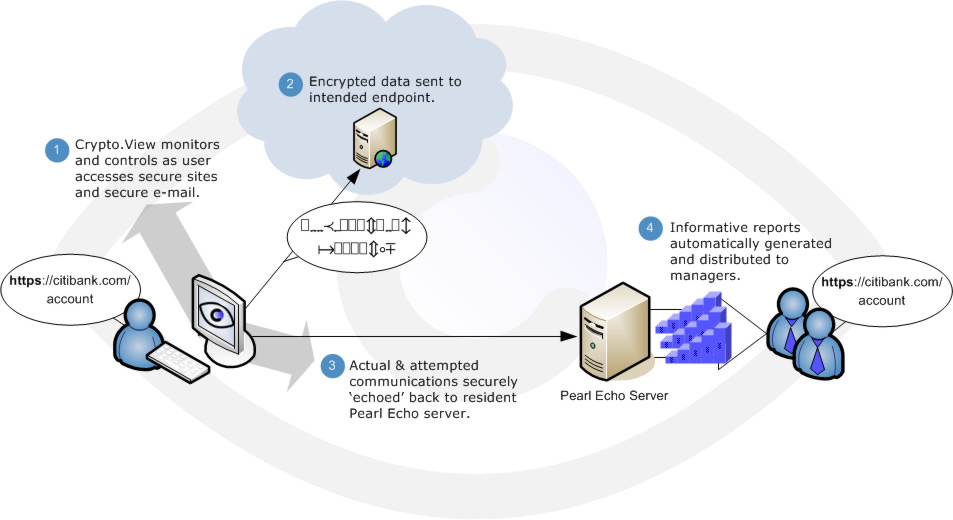
As depicted above, Echo Crypto.View allows you to securely view and control encrypted data without the use of complicated proxy servers or Internet traffic redirection. No shims. No plug-ins. No worries!
Download a Free Trial ...to get a hands-on look at Pearl Echo's features and functions
Start the Pearl Echo.Suite Product Video Tour ...to get a quick look at Pearl Echo's capabilities without installing.
View Pearl Software vs. Competition ...to see how Pearl Software stacks up to the competition.
Request a Quote ...to receive personalized pricing that matches your requirements.
